….
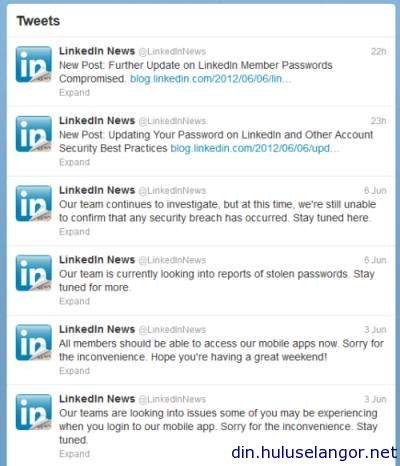
UPDATE: LinkedIn confirms hacking. Read more here.
A user in a Russian forum is claiming to have hacked LinkedIn to the tune of almost 6.5 million account details. The user uploaded 6,458,020 hashed passwords, but no usernames. It’s not clear if they managed to download the usernames, but it’s likely that both have been downloaded.There is a possibility that this could be a hoax, but several people have said on Twitter that they found their real LinkedIn passwords as hashes on the list. Many of the hashes include “linkedin,” which seems to add credence to the claims.
We spoke with Mikko Hypponen, Chief Research Officer at F-Secure, who thinks this is “a real collection.” He told us he is “guessing it’s some sort of exploit on their web interface, but there’s no way to know. I am sure sure LinkedIn will fill us in sooner or later.”
It’s worth noting that the passwords are stored as unsalted SHA-1 hashes. SHA-1 is a secure algorithm, but is not foolproof. LinkedIn could have made the passwords more secure by ‘salting’ the hashes, which involves merging the hashed password with another combination and then hashing for a second time. Even so, unless your password is a dictionary word, or very simple, it will take some time to crack. We’ve reached out to LinkedIn to determine the accuracy of the claims, but in the meantime, we recommend changing your password just in case.
Update: LinkedIn has just tweeted that it is looking into the matter.

Update 3: Security researcher Steve Gibson has highlighted a website which will check if your password can be found on the list of stolen hashes. Bear in mind if you have a common password a positive result may not mean that your account has been compromised.